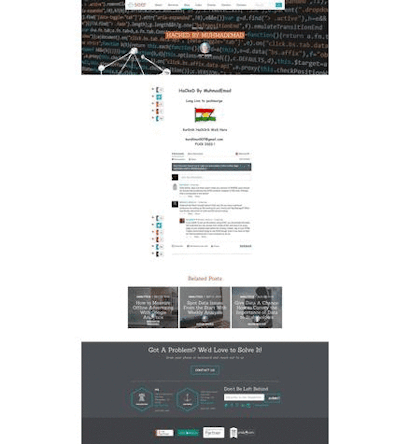
On the 6th of February 2017, a large number of WordPress websites were hacked, one estimate stated as many as 1.5million. Fortunately, the attack was not dangerous, but was simply a content injection which altered the latest blog posts of susceptible websites with the following message:
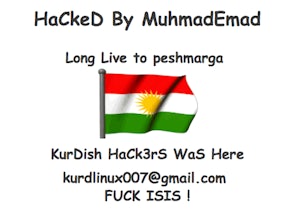
So how did this happen?
Webmasters who failed to update their WordPress sites to 4.7.2 after the potential 4.7.1 issue was announced on the 1st of Feb were at risk of the injection of such content.
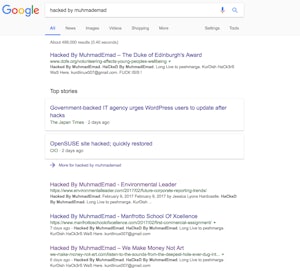
Searching “HaCkeD By MuhamadEmad” brings up a multitude of websites that are currently ranking for the term. The majority of websites have removed the injected content but examples can still be seen through Goggle’s cached screenshots of the sites.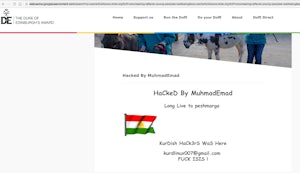
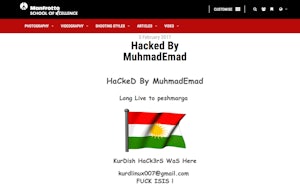
Affected sites included the likes of The Duke of Edinburgh’s Award and the Manfrotto School of Excellence.
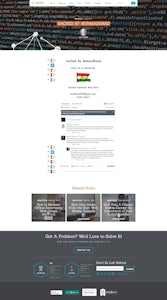
The message

As distant as this may sound from being a conventional digital PR campaign, the attack’s success has gained online media attention.
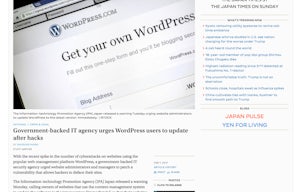
This stories made it to the Japan Times.
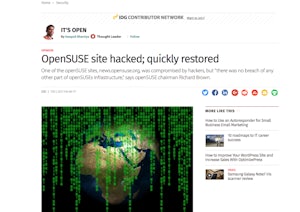
The CIO.
And even, BBC News!
Although a forceful approach to digital PR, the “campaign” has definitely unconventionally gone viral (in its own respect).
What can we learn for this?
Securing your WordPress Site
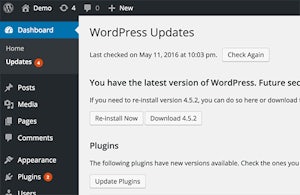
Update, update, UPDATE! Making sure your WordPress site is updated to the latest 4.7.2 version is a must! Although by default every site has automatic updates enabled for minor core releases and translation files, if your server isn’t properly configured, then automatic updates may not work. That’s why it’s best practice that webmasters check their WordPress versions are set to be updated. Fortunately for webmasters who fell victim to the content injections, the attack was fairly tame.
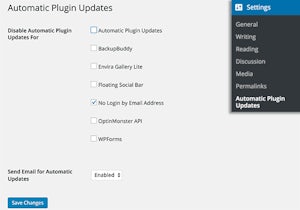
Turning on auto-updates for your plugins will be another simple way to avoid falling vulnerable to such attacks. But this is only advisable in some circumstances. it may sound like a simple enough procedure, but if the circumstances are right, this can be a great way to keep your plugins updated.
Interpreting the attack as digital PR
The attack was definitely a success. The message made it to both owned and earned media sources – digital PR professionals take note.
Trying to get features within such media sources is understandably a challenging task. But maybe we need to stop thinking about the whole create a story, contact the editor approach, and wait for a response approach. Could a thought provoking piece of digital content simply do the job?


